Create and manage LDAP directory for Active Directory in vRealize Automation
Identify Stores can be created and managed by the Tenant Administrator within their specified tenant. They can do this under Administration>Directories Management>Directories

To add an LDAP directory for Active Directory select the “Add Directory” button and specify “Add Active Directory over LDAP/IWA”
To configure Active Directory over LDAP, select Active Directory over LDAP and complete the required fields.
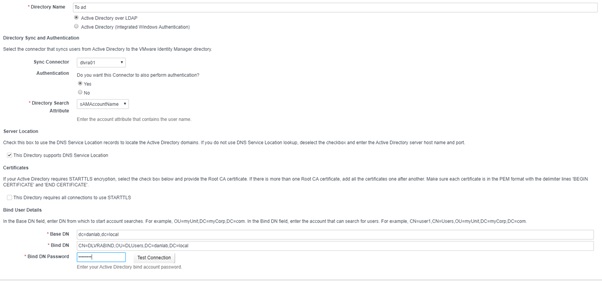
- Directory name – The name of the AD Domain you want to sync with
- Sync Connector – This will be the device that syncs users from Active Directory, when designing vRA solutions ensure the Sync Connector is as close to a DC as possible
- Directory Search Attribute – The account attribute that contains the Username. In scenarios where a single tenant has multiple directories that may contain users with the same sAMAccountName you may want to specify the userPrincipalName here.
- Server Location – if vRA cant resolve the AD Domain then you can specify a domain controller by IP by unticking this box
- Specify a user account used to BIND to Active Directory
Test the connection to Active Directory to ensure it’s working correctly
Click next and select which domains you want to add, you may see multiple domains depending on your AD forest and associated trusts

Select how you want to map the user attributes from AD into vRAs Identity Manager. In the screenshot below I have included a screenshot of my Active Directory user information.
By default you will need to provide two values for the vRA manager attribute and the vRA displayName attribute. In vRA you can choose how you want a users name to be displayed, i’m choosing to use the AD attribute or the same name, displayName. You may want the vRA displayName attribute to be the sAMAccountName or something completely different. I’m using the AD title attribute for the vRA manager attribute

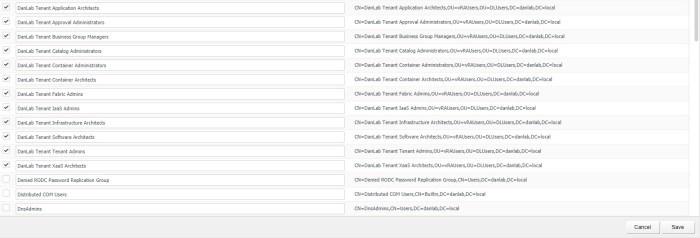
Select which groups you want to sync with vRA, depending on how big your AD structure is depends on how you want to search for groups, I specified the base DN of my whole lab as I only have a few groups in AD, you may want to be more specific with your searches

Hit select and Specify the AD groups you want to sync

Hit next and specify any users not in a group who you want to have access, you can also add a filter to exclude any users by an account attribute, here I’m stopping anyone with the attribute division set to marketing from being added to vRA. Those monkeys are too busy eating unicorn sandwiches to know what they’re doing…

Perform the initial sync of the directory service and keep in mind that the default sync period is a week, in real world environments you’d want to change that to suit your environment. You can do that now by clicking the edit button

Once the directory service has been added, you can force a sync by selecting the directory from Administration>Directories Management>Directories and then hitting the “Sync now” option

If you didnt hit the edit button during the creation of the directory service, you can change these settings retrospectively by hitting the “Sync Settings” button as well as checking which domains are syncing, what the AD mapped attributes are mapped to in vRA Identify Manager, also the groups and users who have been sync

Create and manage Windows Integrated Authentication Directory in vRealize Automation
Identify Stores can be created and managed by the Tenant Administrator within their specified tenant. They can do this under Administration>Directories Management>Directories

To Create and manage Windows Integrated Authentication Directory, select the “Add Directory” button and specify “Add Active Directory over LDAP/IWA”
Select Active Directory (Integrated Windows Authentication)
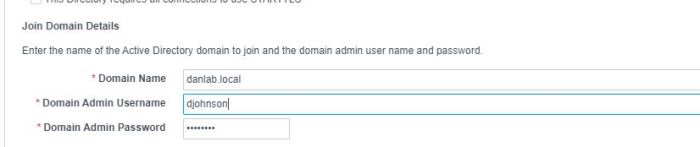
Completing the configuration of this option will add the vRA appliance to the domain

Firstly I got the following error

So i changed my configuration to suit
I subsequently got a new error
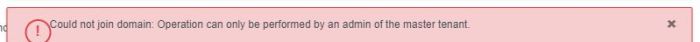
This is because you must setup Active Directory in the default vsphere.local tenant before it can be added to other tenants.
In order to do this, you will need to log into the default tenant.
The default tenant can be accessed – https://myvraserver.mydomain.local/vcac/
If you’ve not setup your default tenant yet and dove straight into configuring a new tenant, then you may need to create some local users within your default tenant and add the new local user as a tenant admin of the default tenant.
Details of how to do that can be found in my Section 2 Object 2.1 blog
Add the Active Directory (Integrated Windows Authentication) identity source in the default tenant, with a tenant admin of the default tenant. Follow the wizard through, after the initial configuration page, the process of stepping through Windows Integrated Authentication Directory setup is the same as Active Directory over LDAP setup.
Once this has been completed in the default tenant, you can log on to subsequent tenants and add that domain as an Active Directory (Integrated Windows Authentication) identity source in the same manner.
When vRA is configured with Active Directory (Integrated Windows Authentication) vRA will use it’s computer account for authentication.
Determine and configure appropriate user and directory binding details
Ensure you have properly thought through the Active Directory bind details, ensuring you use a service account to bind to active directory and that your search DNs are not too broad.
As with every configuration, only what is required should be configured.
Evaluate directory synchronization health and troubleshoot issues
Once you’ve added your directory you can check for issues by selecting the domain from under Administration>Directories Management>Directories
From here you can then check the Sync Log to ensure that syncing has\is working OK
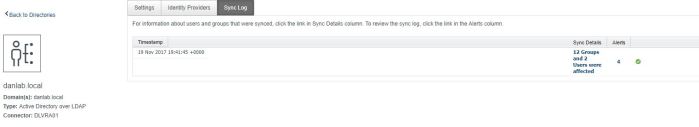
You can set safeguards that will prevent the removing or adding of too many users\groups during a sync operation if required

vRA uses the Identity Manager from horizon. If you look at the vRA appliance you will be able to see the following directory
/storage/log/vmware/horizon
if we list the contents of that folder we can see a connector.log file

if we grep the log file for our LDAP configured Domain Controller we can see entries relating to our LDAP configuration, see this file can also be used for troubleshooting

Tools
[…] We have already created a Directory service that allows us to assign directory users to a business group (in the case of my lab Active Directory LDAP) in Objective 2.2 […]
LikeLike
[…] search for a directory user or group that has sync’d with vRealize Automation (as detailed in Objective 2.2) and assign roles to these users or groups […]
LikeLike